Cloud services bring a momentous opportunity to accelerate business through their ability to quickly scale the business, allowing us to be agile with our resources, and providing new opportunities for collaboration.
As all organisations take advantage of the cloud’s benefits, there’ s one thing we mustn’t forget – our data.
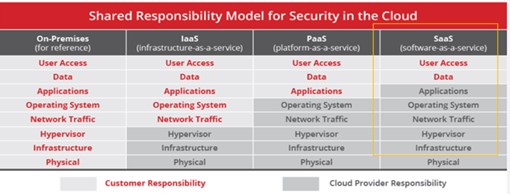
When using software as a service (SaaS), we are responsible for the security of our data, and we need to ensure it is assessed appropriately. When using infrastructure as a service (IaaS) or platform as a service (PaaS), we are additionally responsible for the security of our workloads and need to ensure [1] that the underlying application and infrastructure components are not misconfigured.
The internet security company McAfee published in 2019 a Cloud Adoption and Risk Report[2], and in this article I wish to present some of the most salient points.
McAfee has performed an analysis of billions of anonymized cloud events and determined that nearly a quarter of the data in the cloud is sensitive, and that sharing of sensitive data in the cloud has increased 53% year-on-year. Therefore, if your organisation doesn’t appropriately control access and protect your data from threats, your enterprise is at risk.
Breaking Down Sources of Cloud Data Risk
The use of cloud service is ubiquitous – many of our organisations couldn’t function today without the cloud. Critical to this growth is the understanding that data, and most importantly sensitive data, must be protected.
Specifically, with the rise of the popularity of Office 365, we see an ever larger increase in sensitive data flowing through cloud-based email, primarily Exchange Online. Email remains one of the easiest vectors for data loss and moving it to the cloud removes visibility for IT teams that could before monitor SMTP [3] traffic on their own servers. As the proportion of our data shifts from servers we own to services we use, so does the potential risk increase. It’s critical that we understand what goes into the cloud, so that we can protect it.
When Sharing isn’t Caring – Cloud Collaboration as a Blessing and a Curse
Our data lives in the cloud, and as their analysis showed, nearly a quarter of it requires protection to limit our risk. However, the risk of exposure is counter to one of the key tenets of many cloud services – collaboration. Cloud productivity suites like Office 365 are used to increase the fluidity of collaboration. But collaboration means sharing, and that sharing can lead to the loss of our sensitive information.
Looking at global cloud use today, the survey shows that 48 % of all files in the cloud are eventually at some point shared. Looking more closely at where cloud files are shared, two categories immediately raise red flags:
1) personal email addresses, and
2) anyone with a link (these two categories cover 28 % of all shared files).
Anyone using a corporate cloud account and sending data to a personal email address is invariably removing that data from any oversight by the information security team. Even worse however is data shared to anyone with an open link, potentially leading to an uncontrollable sprawl of data to completely unknown individuals and organisations. Therefore, to reduce the risks to the organisation it’s imperative to understand and control how sensitive data is being shared.
You Can Bet Your IaaS is Misconfigured – So Don’t Forget the Basics
Data doesn’t just live in SaaS applications like Office 365. Amazon Web Services (AWS) has been driving the transformation of server and data center infrastructure to cloud-based services, classified as IaaS and PaaS. The draw is undeniable.
Servers are expensive to buy and maintain, not to mention slow to roll out. The ability to rapidly scale, and the boost in agility are far too compelling to ignore.
Naturally, this isn’t just the AWS show. Microsoft has Azure, and Google their Cloud Platform, among others. The consequence here is a matter of visibility and management. When our infrastructure runs in two [4] or more providers’ systems, much like using multiple SaaS apps, are we sure that we have consistent security across them?
It was found that on average, enterprises have 14 misconfigured IaaS instances running at any given time, resulting in an average of 2.269 misconfiguration incidents per month. Misconfiguration “sounds” bad on its own, but do we really care? When organisations McAfee works with turn on Data Loss Prevention, they detected sensitive data that either shouldn’t be there, or that requires additional monitoring and security controls. All told, 27 % of organisations using IaaS/PaaS have experienced data theft from their cloud infrastructure.
In addition, when looking at the AWS universe, we can see that 5.5 % of all AWS S3 buckets [5] have “world read” permissions, meaning they are fully open to the public. Lastly, we see that enterprise organisations have at least 1 AWS bucket set, giving anyone in the world access to inject their own data into our environments. It is like a free-for-all for anyone trying to compromise our organisations. Want to modify our records? Help yourself. Want to inject malicious code? No problem. It is vital therefore to check for and shut down the S3 buckets we own as well as the ones from 3rd and 4th parties.
Internal and External Threats
Security incidents are no longer isolated to PCs and applications on the network. The average enterprise experiences 31.3 cloud-related security threats every month. These include insider threats (on average, 14.8 incidents each month), privileged user threats (on average, 4.3 incidents each month) and threats arising from potentially compromised accounts (on average, 12.2 incidents each month).
As the number of cloud services and cloud users has grown, so has the amount of cloud activity. The average organisation today generates more than 3.2 billion unique transactions [6] in cloud services each month. With this volume of data, it would be impossible to manually search through an audit trail of user activity to identify potential threats. In response, organisations are investing in user and entity behaviour analytics tools to identify anomalous events (on average, 3 217 anomalous events per month) against the background noise of everyday activity. Out of these 3 217 events, 31,2 threats per month were detected.
More than 30 cloud threats month after month is significant.
Any one true positive threat can compromise both the organisation and brand. The volume of data described above clearly demonstrates that without effective behaviour analytics, the sheer volume of false positives would have inundated the capability to detect and respond to those 30 real threats.
Cloud Usage Trends
More cloud services are launched in the IT market every week. The average enterprise organisation now uses 1.935 cloud services. Broken down by service type, enterprise applications (e.g. Office 365) account for 70 % of cloud services in use.
No two cloud service providers offer the same set of security controls. Across over 25 000 cloud services in use today, only 8 % meet the strict data security and privacy requirements of enterprises. Digging deeper, we find that fewer than 1 in 10 providers encrypt data stored at rest, and even fewer support the ability for a customer to encrypt data using their own encryption keys. Furthermore, given the prevalence of data breaches caused by stolen credentials, it is alarming that only 19.2 % of cloud services support multi-factor authentication.
What happens to data once it is uploaded to a cloud provider? Fewer than half of providers specify that customer data is owned by the customer (the rest either claim ownership over all data uploaded, or don’t legally specify who owns the data). An even smaller number of cloud providers delete data immediately on account termination, with the remainder keeping data up to one year, some even claiming the right to maintain copies of data indefinitely.
Of the 1.935 cloud services in use at the average organisation, 173 (8,9 %) of them rank as high-risk services.
Perception vs Reality – Total Cloud Services
In April 2018, McAfee published a report based on a survey of over 1.400 IT professionals across 11 countries. Each respondent was asked over 100 questions about their organisation’s cloud use.
First, the respondents were asked to estimate the total number of cloud services they believe are in use in their organisation. The average response was 31, with only 2 % of respondents believing that they had more than 80 – yet in reality the average is 1.935. The perception gap is shocking, meaning that 98 % of cloud services are not known to IT – leading to obvious cloud risk.
Perception vs Reality – “Over Trusting” Cloud Services to Keep Data Secure
In the survey, we asked respondents how much they trusted their cloud providers to keep their organisation’s data secure. 69 % of respondents said that they trusted the cloud providers to keep their data secure, and yet cloud security is a shared responsibility and no cloud provider delivers 100 % security. It’s likely that organisations are underestimating the risk they are entering into by trusting cloud providers without applying their own set of controls.
What does all this mean for Internal Audit/Internal Control activities?
According to McAfee, there are 3 key areas we should dedicate some of our audit resources to in future:
- Perform an audit of AWS, Azure or other IaaS/PaaS configurations before they open a major hole in the integrity of our security posture.
- Understand which cloud services hold most of our sensitive data and reduce our risk exposure by proposing an extension of data loss prevention policies to control what can enter or exit them.
- Eliminate lock down sharing by advising the review of where our sensitive data lives and taking action to eliminate “anyone with a link” and limit the sharing of “personal email addresses”.
[1] For details, please see – Figure 1: Shared Responsibility Model for Security in the Cloud – page 3 in this article
[2] https://www.mcafee.com/enterprise/en-us/assets/skyhigh/white-papers/cloud-adoption-risk-report-2019.pdf
[3] The Simple Mail Transfer Protocol (SMTP) is a communication protocol for electronic mail transmission
[4] 78 % of organisations are currently using both AWS and Azure together, typically as an official multicloud strategy.
[5] An Amazon S3 bucket is a public cloud storage resource available in Amazon Web Services’ (AWS) Simple Storage Service (S3), an object storage offering. Amazon S3 buckets, which are similar to file folders, store objects, which consist of data and its descriptive metadata.
[6] Such as user login, upload file, edit document, and so forth