Operational resilience and personal data protection are two topics that are high on the agenda of most organizations these days, as the focus on continuous operations and data privacy are being fueled by the disruptive effects of the Corona virus on business and the excitement around the GDPR and the menace of its large fines and with news of personal data leaks spreading on social media at the speed of a Tweet.
Personal health and safety and economic well-being are of utmost importance and there are some concerns that, given the current extreme circumstances, personal privacy may be given less priority or may be impractical or impossible to sustain.
Companies have become more critical of their vendors and business partners and have learned to value reliability and maturity in a supplier. Recent events will only lend to further focus that attention on the vendor’s ability to maintain operations during a crisis, recover from significant disruptions, survive a financial crisis and also comply with their obligations in regards to data privacy.
Adding to this, suppliers are more integrated in the core business / mission critical decisions of their customers these days. For example, financial institutions using third parties to help value their assets for their clients, health services institutions using third parties to perform clinical research, telecom companies using third parties to help restore their operations in the event of a disaster and manufacturing companies using third parties to provide them with critical components for their production are just a few examples of how critical suppliers can be to a company. Supply chain is one of the hottest rising concerns globally with, for example, the meat industry in the U.S. starting to show concern over being able to meet production needs due to the effects of the pandemic on the workforce.
On top of all of these ‘real’ risks, the explosion in the use of social media has increased the speed at which economic loss or reputational damage can be realized. The effects of an incident can be felt almost immediately. Based on the Deloitte Extended Enterprise Risk Management Global Survey 2019, 83% of organizations experienced an incident at one of their third party suppliers / partners in 2019 with 11% of those being severe and 35% having a moderate impact. These incidents affect not only the supplier themselves and their customers’ but the customers of the those companies that make use of their services. For example, if a significant IT vendor experiences response issues due to understaffing in critical functions due to the effects of the pandemic, not only will their customers have issues (e.g., poor response time, limitations on system maintenance) but the ‘customers of their customers’ may also be affected (e.g., delays in processing of orders or in delivery). You can definitely get a company’s attention by affecting their customer satisfaction ratings and these types of incidents will be considered when renegotiating a contract or evaluating the decision to switch providers.
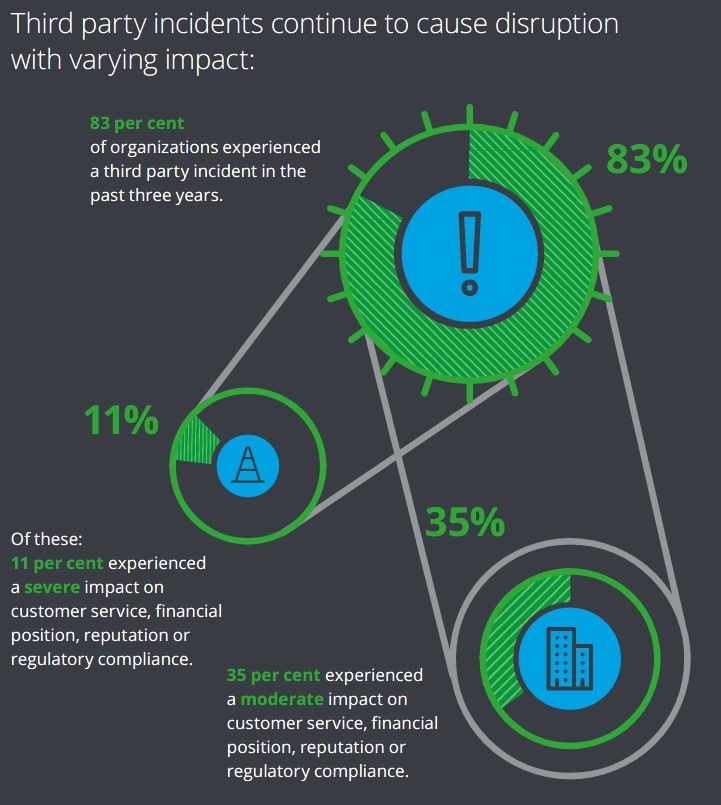
Figure 1: Third Party Incidents
Being advisors to clients on both sides of the customer and supplier equation and seeing the impact this is having on each gives us some interesting insight into the complicated issues arising.
- ‘Customer-side’ challenges – When assisting companies in developing their supplier risk management program maturity, we experience that some companies have a decentralized approach to managing and following-up their supplier relationships. Having a centralized, controlled and mature approach to vendor management seems to have the magical effect of improving the output from a company’s vendors and on the maturity of their internal control environments and compliance efforts. Such a mature approach even seems to position the company to be in a more advantageous position when it is time to renegotiate contracts with suppliers or to enter into new supplier relationships. Our recent experiences with mature vendor management programs indicates that companies expect more from their vendors in regards to being able to evidence their ability to survive and provide services given complex and difficult times as well as being able to provide continuous protection of the sensitive information being shared with them.
- ‘Supplier-side challenges – When assisting suppliers with their programs for evidencing compliance (e.g., attestation reporting like ISAE3402 / SOC 1 or SOC 2), especially with ‘younger organizations’, we see a focus on the areas that ensure the quick delivery of services to customers (e.g., product development and maintenance / support). This may seem like a logical and beneficial trait, but speed is sometimes the enemy of control and a well-balanced program combining control with a focus on delivery is vital to ensuring long-term customer relationships. These vendors are being asked to provide hard evidence that they have ‘control’ in many ways (e.g., economic, delivery capacity and quality, compliance, etc.).
Supplier monitoring
When designing a program for vendor management, it is important to identify all vendors / suppliers as well as the key factors to be used to measure their relative risk to the company. Equally important is determining the factors which you will consider when assessing their performance level. Some examples of factors for consideration in a supplier evaluation program include the following:
- Number of and criticality of services provided (breadth of services)
- Vendor reputation and available ratings
- Cost and financial relationship including pricing (breadth of services)
- Operational performance (Governance)
- Compliance with legal requirements and other key requirements important to the customer (e.g., DPA, Disaster Recovery, ability to evidence adequate internal controls related to the processing of financial information) (Transparency)
- The type, sensitivity and amount of information (e.g., personal data) being shared
- The use of sub-contractors, geographical location, etc.
Some of these would require complex data gathering and analysis processes to be effective. Measurement should be well thought through with identification of data points for measurement, KPI’s, reporting requirements and even assessments.
Having identified all of your vendors and performed a preliminary assessment based on your chosen criteria, each vendor should be categorized, for example from insignificant up to critical. For each category, you would define a set of specific requirements for follow-up and monitoring, with an increase in complexity and effort as the rating gets higher. It is important to define your categories and the requirements for each rating, see the example below.
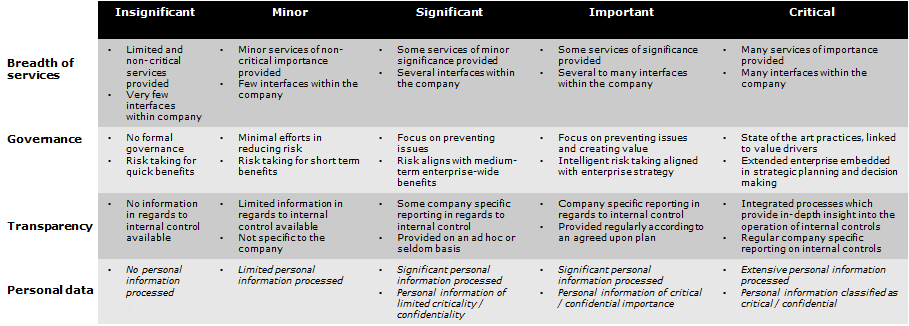
Figure 2: Classify your suppliers (example)
Once each vendor is put in its category, the appropriate measurement criteria should then be applied and monitoring activities put in place to identify instances where vendors are not performing as desired.
Based on the risk profile of the individual vendors and their performance, follow-up steps should be taken, the most common methods being:
- Self assessment – the issuance of self-assessment questionnaires to gather more information. The company may choose to have all of their vendors provide them with a self-assessment as a data gathering exercise or they may choose to only perform this exercise with lower risk entities to get an indication as to their compliance. These types of surveys generally provide low levels of assurance, but the information gathered can be used to further profile vendors and identify candidates for more close follow-up.
- Independently issued certifications and attestation reports – increased requirements on the suppliers to provide proof of either a certification or an independent attestation report addressing specific aspects of the services being provided. Based on the services being provided and the specific area(s) of risk needed to be addressed, the customer may require different types of certifications or attestation reports.
Certifications are often high-level and often supply only a limited level of assurance. Attestation reports often provide a higher level of assurance due to the specificity of scoping to specific focus areas along with more stringent verification requirements for attestation. Attestations can either be generic covering multiple clients of the supplier or customer specific.
- Follow-up audits of selected suppliers – supplier specific audits can be designed to address the specific areas of concern for the company and can provide a high level of assurance, depending on, among other things, the competence of the team performing the audit in relation to the specific audit requirements and the amount of time allocated to the audit. the company may choose to perform follow-up procedures at the supplier(s), based on their agreement with the supplier(s) and the contractual possibility to do so. Many data processors would like to limit the access the data controllers have to perform audits, but this is not generally technically possible due to the contracts / DPAs in place.
Performed properly and thoroughly, with persons competent in the subject matter under review, these can provide a high level of assurance to the company. These can be costly for the company and the resources available to perform these reviews may be limited but this can be supplemented through the use of external consultants with a specialty in performing these types of reviews.
- Operational resiliency / business resumption audits – the areas of operational resiliency and business resumption (disaster recovery) are common topics for IT auditors. Understanding how well a company has planned for bad times and how well prepared they are to recover when the worst case scenario becomes a reality is vital to evaluating your own chances for significant disruptions if that company is supplying you with significant / vital services to your own value chain. We are experiencing a real-life global crisis right now as we write this and there is a lot of uncertainty as to how well companies are prepared to handle the stress put on the organization, its resources and its people.
- Privacy audits – Compliance with privacy requirements is generally as defined in a DPA between a customer and their supplier. There are a number of methods to obtain assurance in regards to a supplier’s adherence to the DPA requirements.
- One of these is to use the new ISO27701 set of criteria in combination with ISO27001/2 to measure a suppliers system for GDPR compliance. ISO27701 and ISO27001/2 are logical measurement criteria which can be used to define the in-scope processes and controls at a supplier. ISO27701 (privacy enhancements to ISO27001) was issued in August 2019.
- Another common method is to use the specific DPAs in place and develop a set of criteria to be used as the basis for measurement. Standard best practice controls could be used to determine the adequacy of identified controls to meet the defined control objectives.
Regardless of the criteria chosen, the areas common to most privacy audits include:
- Strategy – The privacy strategy defines the scope and objectives, setting the direction and goals for all other GDPR topics
- Organization and accountability – The privacy strategy is implemented by assigning people with responsibilities as well as a clear mandate and resources
- Policies, processes and procedures – Privacy must be an integrated part of the internal control framework. This means updating governing documents or developing new ones to address GDPR as well as the internal privacy strategy
- Communication, training and awareness – The new policies, processes and procedures must become an integrated part of the culture and some information needs to be communicated externally as well
- Privacy operations – Concepts such as privacy by design and default must be supported by tools and methodologies (e.g., a data protection impact assessment methodology as part of the project framework)
- Processing inventory – A fundamental concept for privacy is the processing inventory. An overview is a legal requirement for the processing operations, including which personal data is involved.
- Technology – Most information today is stored, processed and transported using IT. The operational activities and reporting on privacy related risks often require technology to ensure adequate quality and efficiency
The effect of the pandemic on the audit approach
Given the current situation, those of us that work with audit / attestation have also realized a specific set of risks related to obtaining evidence to support our work as well as the quality and reliability of the documentation our customers’ may (or may not) be able to provide us as evidence of control execution. Our guidance indicates that we need to be professionally skeptical, critical of documentation such as scanned evidence which we would normally be seeing ‘live’ and which may be manipulated and thorough when it comes to gaining assurance in regards to control operational effectiveness testing, especially in the period where companies’ were affected by the pandemic. What if, for example, we are unable to obtain evidence related to a selected item in a testing population because the client can’t locate the supporting documentation while working remotely? This skepticism and need for comfort from our clients’ rolls down through to the customers’ subservice providers and vendors of significant services.
Increased demand for attestation reporting
We have seen a sharp increase in the interest in attestation reporting (e.g., ISAE3402, SOC 1 or SOC 2) in general and in more recent months, data privacy agreement attestation specifically. This increase in interest is being driven by businesses pressuring their data processors to evidence their compliance with GDPR and DPA requirements. The requirement for this type of assurance is often a contract requirement, inserted in renegotiations or as part of RFP’s.
As a result of the Corona pandemic, we expect that there will be a stronger focus on the areas of operational resilience and business resumption (disaster recovery planning) in regards to the scoping of our attestation reports. Vendors will want to assure their customers that they are well prepared and the customers will be focused on ensuring that their supply chains will not be broken.
As awareness of the risks related to third party relationships grows, so will the focus on mitigating such risks. Our survey showed that there is still a ways to go in regards to this, with 50% of respondents not even in a good enough position to understand the nature of individual third party relationships.
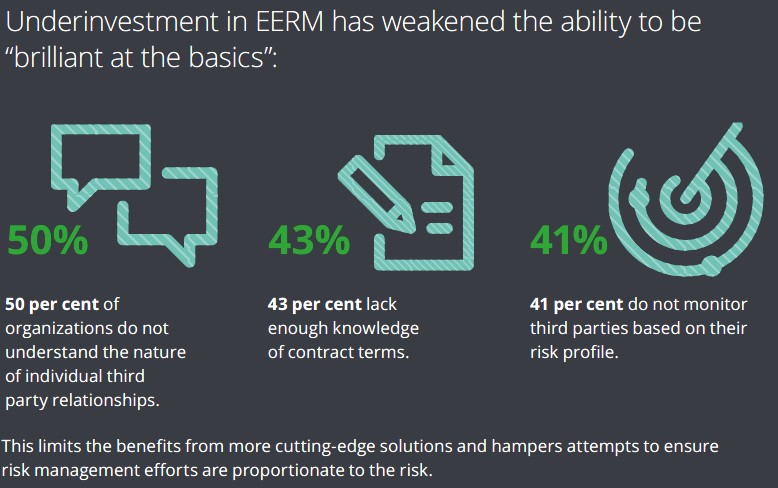
Figure 3: Stats related to Third Party Monitoring
Conclusion
As companies become more mature in their own processes for managing third party relationships and more specifically operational resilience and personal data processing, we expect that their focus on ensuring that they enter into and maintain only ‘good’ relationships where they feel comfortable with the vendor’s ability to deliver quality service balanced with a good dose of adequate control will increase.
The risk of non-compliance is ever growing and companies are more focused on their relationship management processes as well as ensuring their compliance to regulations, including ensuring compliance though to their third party relationships. Time will tell how the pandemic will affect areas such as personal data privacy and concerns about vendor / supplier management.
A well-organized vendor management program, based on criteria that meets the needs of the individual company and providing accurate and timely data in regards to vendor management, is an important tool to ensure that a company gets the most out of its vendors while also ensuring its own compliance through to its subservice providers. Centralizing the overview of suppliers and their relative risk to the company and performing regular analyses of the key factors related to their delivery and compliance is important for the company’s own future survival.